This is part three of a series, ‘Lessons from the first cyberwar.’ Read part one and part two.
Over the past two decades, warfare has expanded beyond mere physical confrontations to encompass the digital realm.
As a result, cyber capabilities have been growing, leading nation-states, notably Russia and Israel, to use cyberattacks increasingly in support of their political objectives as the following case studies illustrate.
Estonia 2007
In the spring of 2007, Estonia experienced what came to be known as the first cyberattack on a nation-state. This campaign was linked to a wider political dispute with Russia over the relocation of a Soviet-era monument in Tallinn. The cyberattacks, which began on 27 April, targeted Estonia’s internet infrastructure, including banks, media outlets and government services.
The cyberattacks were mostly Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks. They overwhelmed servers with massive waves of network traffic sent from botnets and automated requests, disrupting online services at an unprecedented level.
Estonia’s experience was the first instance of a nation facing this modern form of hybrid warfare. The effectiveness of the Russian cyberattacks on Estonia was amplified due to the country’s extensive reliance on the internet. In 2000, Estonia’s parliament even declared internet access a human right and the country has invested heavily in digitization.
These attacks flagged the vulnerabilities in a highly digitized society, demonstrating the risks of embracing extensive digitalization. The attacks demonstrated that cyber warfare is a serious tool for societal disruption in military contexts as it can cause damage but also not be followed with any sort of military retaliation. Following the attack, Estonia established a voluntary Cyber Defense Unit – something that Ukraine is currently considering as well.
A notable aspect of these attacks was their ambiguity as a wide variety of actors including cyber gangs loyal to Moscow conducted the attacks. This practice can enable any state sponsor orchestrating the attacks to remain hidden and deny involvement, as attribution is difficult without proving who is responsible – which is incredibly difficult in cyberspace.
The 2007 attack on Estonia also helped to speed up the creation of the NATO CCDCOE in 2008. It became NATO’s cyber defense center, which today includes over 30 NATO members, with Ukraine having joined the center in 2023.
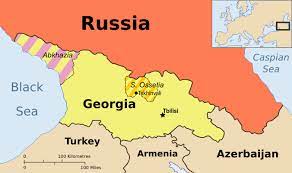
Russia–Georgia War of 2008
In August 2008, during its invasion of Georgia, Russia combined cyberattacks with military actions on the ground. This was the first time such a coordinated effort had been seen in warfare. This Russian-Georgian war stemmed from frozen Russian-controlled conflicts in Abkhazia and South Ossetia, which Georgian President Mikhail Saakashvili sought to end.
This early form of cyber warfare was characterized by its alignment with Russia’s military and political objectives, contrasting with the earlier 2007 Estonia cyber incident. Russia’s strategy focused on controlling Georgian military and government communication channels.
Before the physical invasion, Georgian government sites experienced a pre-emptive cyberattack that began on July 20, 2008; the website of the president was overwhelmed by traffic, including the phrase “Win+love+in+Russia”, and was inoperable for 24 hours.
The attacks intensified on August 8 with a series of DDOS attacks coinciding with Russia’s invasion of South Ossetia. These cyberattacks had effectively disabled most of Georgia’s governmental websites by August 10. Faced with a communication blackout, Georgia sought cyber refuge by relocating critical official internet assets to the United States, Estonia and Poland without prior US government approval.
The primary objective of the Russian cyberattacks on Georgia was to isolate and silence the country. This strategy also included disrupting Georgian banks, which faced a deluge of fraudulent transactions, prompting international banks to halt their operations in Georgia to limit damage.
Consequently, Georgia’s banking system was incapacitated for 10 days. This disruption extended to the shutdown of mobile phone services, further severing Georgia’s communication with the outside world.

Russian hackers also took aim at Georgian commercial websites, causing economic damage akin to the disruption experienced by the banking system. During the attacks, 35% of Georgia’s internet networks experienced reduced functionality. The damage peaked during the Russian invasion of South Ossetia between August 8 and 10.
In response to the cyber onslaught, Georgia initially tried filtering Russian IP addresses. However, Russian hackers quickly adapted, employing non-Russian servers and spoofed IP addresses to continue their attacks. This series of events demonstrated Russia’s ability to effectively integrate cyber warfare with conventional military operations, achieving its strategic goals and setting a precedent for future conflicts.
Russia’s cyber offensive also demonstrated the importance of protecting not only military networks but also civilian computer networks. The attacks catalyzed expert discussions about the concept of a “digital Pearl Harbor,” a scenario in which a nation’s infrastructure is overwhelmed and shut down through internet-based attacks.
Many also predicted that Russia’s 2022 invasion of Ukraine would unleash a “digital Pearl Harbor.”
Kyrgyzstan 2009
In January 2009, Kyrgyzstan was hosting an American military base, the Manas Air Base, which played a strategic role in US military operations in Afghanistan. Russia, seeking to expand its sphere of influence in Central Asia, wanted to reduce the American presence in the region and was negotiating with the Kyrgyz government over the air base.
While negotiations were underway, Russian hackers carried out a DDoS attack against Kyrgyzstan. The attack took out two of Kyrgyzstan’s four main internet service providers.
The cyberattack was part of a broader strategy by Russia to pressure the Kyrgyz government as it coincided with negotiations and discussions regarding the American military base. Following the cyberattack and amidst ongoing negotiations, Kyrgyzstan announced its decision to shut down the American military base.
Russia’s 2009 cyberattack on Kyrgyzstan continued to demonstrate to the Russian leadership the growing role of cyber capabilities as tools of statecraft and how they could be used to threaten or strong-arm countries.
Israel–Iran cyberwar
Since the 1979 Islamic Revolution in Iran, there has been a four-decade conflict between Iran and Israel. The revolution ushered in a new Islamic regime in Iran, which adopted the Palestinian cause and severed diplomatic ties with Israel.
The rivalry has extended beyond direct confrontation to a proxy war, with Iran supporting terrorist groups including Hezbollah in Lebanon and Hamas in Gaza, both of which border Israel.
However, the proxy war would eventually extend into a direct conflict between Iran and Israel in cyberspace. Cyber warfare had become a new front in this conflict by 2010, although the extent remains largely undisclosed as neither nation openly admits to launching cyberattacks against the other.
Israel, often in collaboration with the United States, is suspected of conducting several sophisticated cyber operations targeting Iran’s nuclear program. The most notable attack in the cyber war was the discovery of the Stuxnet virus in Iran’s Bushehr nuclear power plant computers in 2010.

Believed to be a joint creation of Israel and the United States through Operation Olympic Games, Stuxnet was engineered to cause physical damage by speeding up and destroying the IR-1 centrifuges, leading to the destruction of about 1,000 out of 9,000 centrifuges at Natanz.
Stuxnet effectively disrupted production at Natanz by damaging the facility’s equipment. Iran attributed this attack to Israel and the United States.
In response to the Stuxnet incident, Iran significantly bolstered its cyber capabilities, enhancing both defensive and offensive measures. Between 2012 and 2015, Iran’s cyber security budget increased by around 1200% and, after Stuxnet, Iran began focusing the majority of its cyber espionage against Israel.
At a 2019 tech conference, Israeli Prime Minister Benjamin Netanyahu claimed that Iran was constantly conducting cyberattacks that targeted Israel’s critical infrastructure.
In April 2020, Israel experienced a cyberattack on its water and sewer facilities, leading to temporary disruptions in local water systems. Initially attributed to a technical malfunction by the Israeli government, it was later identified as an attack by Iran.
In response, Israel launched a retaliatory cyberattack the following month against the Shahid Rajee Port, targeting the operating systems of private shipping companies. The consequences were widespread, causing prolonged road and waterway congestion.
The Iranian attack on Israel was believed to have been targeting the water supply by increasing chlorine in the water that is delivered to residential areas.
Yigal Unna, the head of Israel’s National Cyber Directorate, believed that if the attack had not been detected in time, chlorine or other chemicals could have been mixed into the water supply, poisoning many civilians.
In 2021, Israel was accused by Iran of conducting a cyberattack that took down many of the country’s gasoline stations by sabotaging a payment system, leaving many people unable to buy fuel for their vehicles.
While nations routinely engage in probing each other’s public utilities to identify vulnerabilities and establish a persistent presence, the escalation to actual attacks is a rarity. But if nation-states want to execute large-scale cyberattacks against civilian infrastructure, the consequences could be deadly for the civilian populations.
A comparison of the cases, starting with the cyberattacks on Estonia in 2007, with the complex cyber operations against Ukraine up to 2022 (see the next installment for those) provides insight into how Russia has conducted its cyber campaigns in the past, how its capabilities have evolved and how cyber strategies support political goals.
David Kirichenko is a Ukrainian-American security engineer and freelance journalist. Since Russia’s full-scale invasion of Ukraine in 2022 he has taken a civilian activist role.
These articles are excerpted, with kind permission, from a report he presented at the UK Parliament on February 20 on behalf of the Henry Jackson Society.