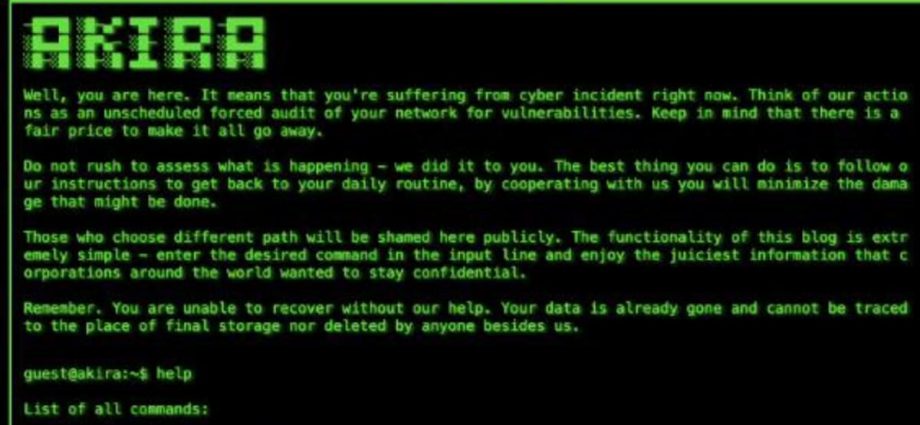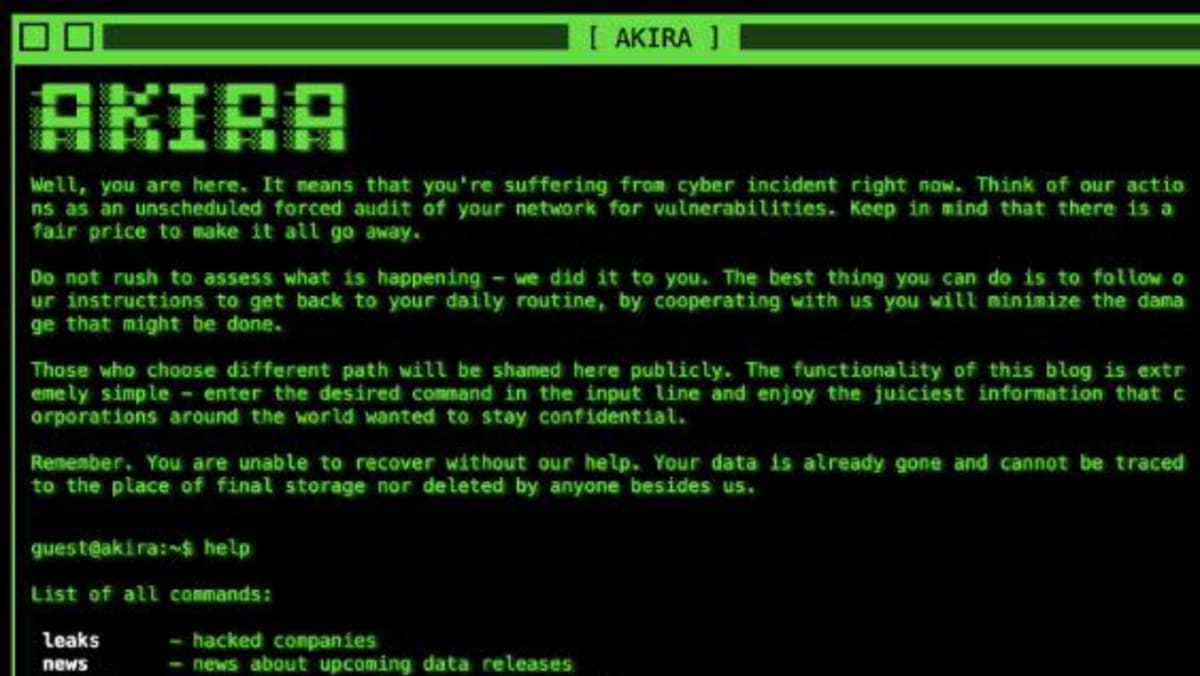
RECOMMENDED Methods
The government advised businesses to implement and constantly monitor the compliance of a number of reduction procedures and policies in order to reduce the risks and effects of a malware event.
Organizations should put in place robust password guidelines that call for the use of strong credentials or passphrases with at least 12 characters of mingled content, including upper case, lower case, numbers, and special characters.
Additionally, they should implement multi-factor authentication to reduce the possibility of illegal access to all internet-facing services, such as VPNs and accounts that access essential systems.
Reliable anti-virus or anti-malware software is, according to the authorities, help identify Akira and other ransomware variants.
” This can be accomplished by real-time monitoring of system processes, network traffic, and report action for indicators of bargain typically associated with the malware,” says the author.
The software may be configured to limit access to sensitive files and folders, prevent illegal remote connections, and encrypt the implementation of dubious files.
” Organisations should regularly scan their systems and networks for vulnerabilities and constantly update all operating systems, applications, and software by applying the latest security patches rapidly, especially for functions essential to the business”, said the police, CSA and PDPC.
Companies that have outdated applications that the engineer no longer supports may switch to more recent alternatives.
Separating systems can even help control traffic flow between thread- systems, limiting the spread of malware. Organizations should also keep an eye on their reports for any suspicious activity and take appropriate restoration measures as needed.
Routine files of significant data may be carried out. The authorities advised businesses to use the 3- 2- 1 guideline when making backups: Maintain three copies of the backups, store them in two unique media formats, and store one set of backups off-site.
Conducting event response exercises and developing , business continuity plans may help strengthen an organisation’s preparation for a ransom harm, they added.  ,
The impact of a data breach will be kept to a minimum while keeping only essential data safe and limiting the collection of personal data.